How Cohesity has embraced Immutability and Air Gap-as-a-Service to enhance your Disaster Recovery Plans
In our recent blog, Immutable Backups and 5 reasons why you need them for your disaster recovery plan, we introduced immutable backups. Now it’s time to dive into the different solutions that are out there, to help you decide which one is the best approach for your environment.
Cyber-attacks have become more sophisticated than ever. They no longer simply corrupt your environment, but your backups too. While many cyber insurance companies have not yet made “immutability” a requirement, we know it’s coming soon. According to NIST SP 800209 Security Guidelines for Storage Infrastructure, “Immutability involves the ability to lock data after it has been created, thereby preventing it from alteration or deletion.” [1]
As promised, we’ve contacted our partners over at Cohesity to take a deeper dive into their immutable solutions and AirGap-as-a-Service virtual vault, FortKnox.
In this blog, we’ll explore the following topics:
- Advice on Building and Effective Recovery Plan
- Cohesity's Data Platform Approach
- Cohesity’s Immutable Methodology
- Data Isolation and Air Gap-as-a-Service
- FortKnox vs. Cloud Archiving
- Interoperability with Your Current Cybersecurity Ecosystem
- Instant Mass Restore Functionality
Here’s what they recommend for data backups and for building an effective Disaster Recovery plan.
Building an Effective Recovery Plan
To get started, we wanted to note that Cohesity has been recognized as the 2022 Gartner Magic Quadrant for Enterprise Backup and Recovery Software [2], so the efficacy of their solutions and methodology is undeniable. With that validation, they’ve outlined some vendor-agnostic advice for you regarding the components of an effective recovery. Here are the four main components you need to Protect, Defend, and Recover according to Cohesity.
Have a Plan and Understand What You Need to Defend
The best offense is defense. What better way to defend, than to first understand what it is you’re defending. To build a plan, you must first identify within your environment:
- System dependencies
- Personal identities
- Communication channels
- Services and facilities
- Technology
- People
- Processes
By understanding this information, you can then build your disaster recovery playbook. This generally includes:
- Well identified initiation and termination criteria and goals
- Recovery steps
- Controlled access controls
- Communication milestones
- Operational workarounds (should a breach/impediment take place)
Define A Team for Root Cause (Attack/Breach) Search and Containment
In this step, you need to discover the threat actor/adversary’s objective. A few examples of such objectives include:
- Encrypting Production Data
- Destroying Backups
- Destroying Access
- Exfiltrating Data
Additionally, your dedicated team must define the full extent of the event and have a solid understanding of the technical mechanism used to access your environment.
The next step is what Cohesity calls, the Tactical Recovery Phase. This includes stakeholders from all business units and focuses on the validation of the actual recovery (where immutability comes into play), and the restoration of services.
Cohesity’s final component of an effective recovery is what they call the Strategical Recovery Phase. This reviews the quality of the recovery and the overall impact on the organization. A few metrics you could use to validate the impact include:
- Legal costs
- Lost revenue due to downtime (current and future opportunities lost)
- Accuracy of dependency maps
- Gaps identified in the playbook (see component 1)
- SLA adjustments
- Internal users
- External business partners
- The impact on the customer’s trust in your organization
The purpose of this final component is to help you better prepare for future events by zeroing in on the actual cost of the breach, and holes in your DR plan.
Cohesity Data Platform Approach
What makes Cohesity different in the backup space is that they have their own data platform, Helios. This platform not only has backup and recovery, but also allows you to add on use cases and features that you need. This is Cohesity’s key differentiator from other backup and recovery providers.
Their data platform:
- Provides Simplicity at scale
- Is Built on Zero Trust Security Methodology
- Can account for 3rd party extensibility
- It’s designed to accommodate new features and functionalities!
- Is AI Powered
Hackers won’t be able to simply identify your defense blueprint and work around it. The AI adapts to the issues, allowing you to quickly identify anomalies and act.
Cohesity’s Immutable Methodology
Cohesity offers an ecosystem friendly immutable backup solution in addition to some tried and true methodology, like data isolation, and their AirGap-as-a-Service solution, FortKnox, which we will cover shortly. This is often referred to as Cohesity’s Threat Defense Architecture. Their immutability isn’t just a part of one solution, it’s a part of their entire methodology. Some of the key benefits they offer to protect your data include:
- Immutable backup snapshots
- Robust encryption algorithms
- Erasure coding
- WORM (DataLock), and more
Cohesity strives for fast and accurate ransomware detection. This makes ransomware recovery more effective.
Next, let’s dive into data isolation and their AirGap-as-a-Service data vault solution, FortKnox.
Data Isolation and Air Gap-as-a-Service
Cohesity demonstrates why you need to isolate your data by first highlighting the biggest threats to that data.
- Sophisticated ransomware attacks that encrypt your data
- Natural disasters/outages that cause physical damage to your backup copies
- Internal bad actors (disgruntled employees or admin) with authorized access
You need to keep an untouchable version of your data to quickly restore your environment should one of these events occur. This is where the 3:2:1 rule comes into play.
The 3:2:1 Rule
Have 3 copies of your data in 2 different locations/mediums and 1 in a segregated environment. Their solution, FortKnox solves this issue.
FortKnox vs. Cloud Archiving
This is Cohesity’s AirGap-as-a-Service product. It’s available on any of your Cohesity clusters. It is Cohesity’s single solution to vault data for sources including Virtual Machines (VMs), files, databases, etc.
This as-a-service model includes a dynamic connection/ “Virtual Air Gap” which means you create a token that connects to FortKnox, push out the data, and sever the connection. Data sent to FortKnox is completely separated, unreachable, and indestructible.
The benefits of utilizing FortKnox vs. Cloud Archive:
- Managed service access and storage
- 100% immutable (vs. relying on cloud storage WORM and cloud controls for security)
- Built in Quorum workflow
- Unlimited restore from Golden Image
- Predictable cost model (no hidden Egress charges for mass recovery)
- Cyber Insurance rate reduction due to use of True Cloud Airgap with Disconnection
- FortKnox Vault is obfuscated from Cohesity Cluster
- SOC II type 2 and type 1 certification
There are multiple ways to protect your data, and often these methods are combined with others to enhance your security fortitude. While we’ve discussed virtual data isolation and AirGaps which is a better fit for enterprise data simply for convenience, and scalability, there is another option, and that’s physical data isolation.
Physical Data Isolation
This method involves creating a data backup to a physical hard drive and securing it in an offsite location. There are a few key drawbacks to this option. Because enterprise data has grown so large, it requires more physical media to hold all the data.
What makes this method arguably inconvenient is that for it to really function as it should (represent a current data backup), the data must be transported and updated daily which can get costly. Additionally, recovering this data is SLOW. So, if you’re considering physical data isolation, remember that there is a cost to downtime. Finding a solution that costs less than paying the ransom should be the goal.
Interoperability with Your Current Cybersecurity Ecosystem
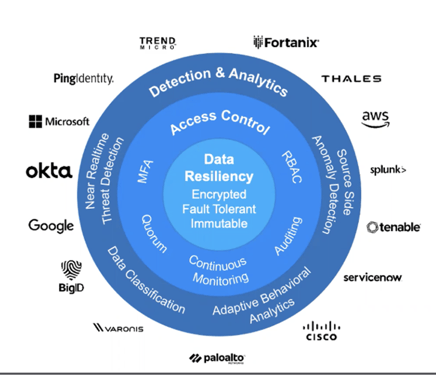
There’s nothing worse than feeling like you made an investment that doesn’t cover all your cyber insurance requirements. The great thing about Cohesity is that it integrates with some of the best-in-class (and most used) security products/vendors, so it SUPPLEMENTS what you have in place, not replaces it. Below are some of the major Cybersecurity names that Cohesity is currently interoperable with.
Cohesity Threat Defense Architecture - Source: Cohesity
Not only is it interoperable, but it will amplify your existing controls. The Cohesity software has integrations to SOAR, SIEM, KMS, and more!
Instant Mass Restore Functionality
One thing that many people don’t consider is the length of downtime that comes with a breach. Your Down Time to Recovery (DTR) means everything. We’ve heard of instances where a company pays the ransom because the cost is less than the revenue they’d lose in their downtime. In extreme cases, businesses can go belly up due to lost revenue and customer trust during that downtime. Fast recovery time is just as important as immutability nowadays, especially when every minute counts.
Cohesity offers functionality that allows for INSTANT mass restore. Which means if your system goes down, you can roll out an uncorrupted backup and get back to business in minutes rather than days. This function allows you to restore uncorrupted data instantly and at scale. It allows you to recover Virtual Machines (VMs), databases, and Network Attached Storage (NAS) volumes instantly on-prem AND in the cloud.
If you are searching for a data backup and disaster recovery solution, you’ll want to consider the speed that you can roll out a backup. It could mean the difference between experiencing minimal ill effects from a data breach or going bankrupt.
Learn More about Immutable Backup Solutions
The truth is cyber criminals likely know what your cyber insurance policy covers. This means they know exactly how much money they can reliably extort from you. They understand that companies unprepared to defend against such attacks will pay the ransom to avoid downtime. What other choice would these companies have? Remember, hackers are unethical, not uneducated, and they will likely leave a back door into your environment to extort you again if you don’t improve your security.
Cohesity's AirGap-as-a-Service platform, FortKnox, their Threat Defense Architecture, and their distinct data platform make them a compelling option when looking for quick and effective data restoration solutions. Note that no matter what platform you utilize for data protection, it will be ineffective if it is misconfigured or if you aren’t performing routine testing. Consider working with an expert upon initial implementation to ensure it is deployed properly.
Depending on the size of your environment and the volume of data you must protect, Cohesity could be an ideal solution, though it’s not the only one. In our next installment we’ll dive into VEEAM’s immutable backup solutions.
Don’t miss out, sign up to get notified whenever we release related immutable backups content.
Sources:
[1] https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-209.pdf
https://www.cohesity.com/glossary/data-isolation/
https://www.cohesity.com/products/fortknox/
https://www.cohesity.com/why-cohesity/threat-defense/
https://www.cohesity.com/next-gen-data-management/threat-defense/