7 Cybersecurity Lessons Learned from the Field
The world of IT has become more complex over the years. If you've ever wondered what IT god you aggravated for cybersecurity to be thrown into the mix and become ever-increasing in priority and complexity, you aren’t alone. There always seems to be some new exploit tactic popping up, new acronyms to be defined, or redefined, and new products to protect your business against new vulnerabilities. How do they all apply to you and what should you be focusing on? While each organization is different, here are the cybersecurity lessons we’ve learned over the past year.
7 Cybersecurity Lessons Learned from the Field:
- LESSON 1: Hackers are waiting for the right time. Several large-scale attacks that are closing out 2018, including Facebook and Marriott, appear to be opportunistic while having the hallmarks and opportunities for Annuity style attacks where the attackers will hold stolen account data and later combine it with other stolen data for future identity theft attacks.
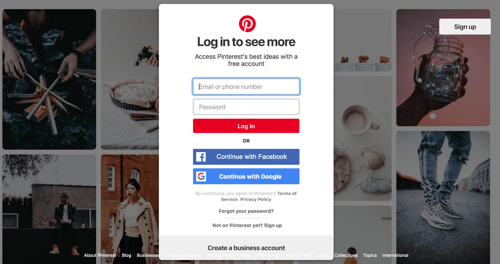
- LESSON 2: Attacks on social media platforms are a concern as many of them, including Facebook, are used for single sign-on for other websites. For example, Pinterest uses Facebook or Google single sign-on to access their site.
- LESSON 3: Hackers are using older data for current phishing campaigns. We believe that many of the recent phishing campaigns which led to successful attacks could be the result of older data breaches and the increased use of Big Data tools to mine stolen data.
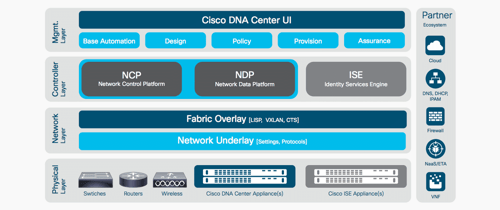
- LESSON 4: Organizations need to look for an opportunity to leverage increased network efficiencies, such as those found in Cisco’s DNA Center, built around the Software-Defined Access concept and Intent-Based Networking.
- LESSON 5: There’s an opportunity to integrate a more robust security posture that’s purpose-built with scalability in mind. What’s opening this opportunity is that businesses are moving toward a more agile workload management model, and traditional network-based security controls, such as VLAN segmentation and access control lists, are becoming part of a defined policy.
- LESSON 6: Organizations have a renewed focus on network visibility based on increased operational efficiency and the ability to recover from a cyber incident as quickly as possible. Tools such as Stealthwatch and Cisco DNA Center enable much more streamlined visibility and analytics.
- LESSON 7: Risk remains the best benchmark to measure an organization’s effective security and its ability to weather a breach. Understanding that risk and the opportunities to mitigate it as much as possible begins with a risk assessment.
Each year, or month, or day, will bring new cybersecurity lessons. In order for you to stay on top of what’s changing, it’s important for you to stay connected to the pulse of the cybersecurity community, your peers, and partner with an organization that can help you find strategic and efficient ways to address your security concerns that keep your business operations, data, and reputation safe. IE has several ways to help keep you connected. We host Security User Groups quarterly throughout the year, and our
For more information on our quarterly Security User Groups, sign-up here.
To contact a member of our